Features
The Lazarus heist: How North Korea almost pulled off a billion-dollar hack

In 2016 North Korean hackers planned a $1bn raid on Bangladesh’s national bank and came within an inch of success – it was only by a fluke that all but $81m of the transfers were halted, report Geoff White and Jean H Lee. But how did one of the world’s poorest and most isolated countries train a team of elite cyber-criminals?
It all started with a malfunctioning printer. It’s just part of modern life, and so when it happened to staff at Bangladesh Bank they thought the same thing most of us do: another day, another tech headache. It didn’t seem like a big deal.
But this wasn’t just any printer, and it wasn’t just any bank.
Bangladesh Bank is the country’s central bank, responsible for overseeing the precious currency reserves of a country where millions live in poverty.
And the printer played a pivotal role. It was located inside a highly secure room on the 10th floor of the bank’s main office in Dhaka, the capital. Its job was to print out records of the multi-million-dollar transfers flowing in and out of the bank.
When staff found it wasn’t working, at 08:45 on Friday 5 February 2016, “we assumed it was a common problem just like any other day,” duty manager Zubair Bin Huda later told police. “Such glitches had happened before.”
In fact, this was the first indication that Bangladesh Bank was in a lot of trouble. Hackers had broken into its computer networks, and at that very moment were carrying out the most audacious cyber-attack ever attempted. Their goal: to steal a billion dollars.
To spirit the money away, the gang behind the heist would use fake bank accounts, charities, casinos and a wide network of accomplices.
But who were these hackers and where were they from?
According to investigators the digital fingerprints point in just one direction: to the government of North Korea.
SPOILER ALERT: This is the story told in the 10-episode BBC World Service podcast, The Lazarus Heist.
That North Korea would be the prime suspect in a case of cyber-crime might to some be a surprise. It’s one of the world’s poorest countries, and largely disconnected from the global community – technologically, economically, and in almost every other way.
And yet, according to the FBI, the audacious Bangladesh Bank hack was the culmination of years of methodical preparation by a shadowy team of hackers and middlemen across Asia, operating with the support of the North Korean regime.
In the cyber-security industry the North Korean hackers are known as the Lazarus Group, a reference to a biblical figure who came back from the dead; experts who tackled the group’s computer viruses found they were equally resilient.
Little is known about the group, though the FBI has painted a detailed portrait of one suspect: Park Jin-hyok, who also has gone by the names Pak Jin-hek and Park Kwang-jin.
It describes him as a computer programmer who graduated from one of the country’s top universities and went to work for a North Korean company, Chosun Expo, in the Chinese port city of Dalian, creating online gaming and gambling programs for clients around the world.
While in Dalian, he set up an email address, created a CV, and used social media to build a network of contacts. Cyber-footprints put him in Dalian as early as 2002 and off and on until 2

013 or 2014, when his internet activity appears to come from the North Korean capital, Pyongyang, according to an FBI investigator’s affidavit.
The agency has released a photo plucked from a 2011 email sent by a Chosun Expo manager introducing Park to an outside client. It shows a clean-cut Korean man in his late 20s or early 30s, dressed in a pin-striped black shirt and chocolate-brown suit. Nothing out of the ordinary, at first glance, apart from a drained look on his face.
But the FBI says that while he worked as a programmer by day, he was a hacker by night.
In June 2018, US authorities charged Park with one count of conspiracy to commit computer fraud and abuse, and one count of conspiracy to commit wire fraud (fraud involving mail, or electronic communication) between September 2014 and August 2017. He faces up to 20 years in prison if he is ever tracked down. (He returned from China to North Korea four years before the charges were filed.)
But Park, if that is his real name, didn’t become a hacker for the state overnight. He is one of thousands of young North Koreans who have been cultivated from childhood to become cyber-warriors – talented mathematicians as young as 12 taken from their schools and sent to the capital, where they are given intensive tuition from morning till night.
When the bank’s staff rebooted the printer, they got some very worrying news. Spilling out of it were urgent messages from the Federal Reserve Bank in New York – the “Fed” – where Bangladesh keeps a US-dollar account. The Fed had received instructions, apparently from Bangladesh Bank, to drain the entire account – close to a billion dollars.
The Bangladeshis tried to contact the Fed for clarification, but thanks to the hackers’ very careful timing, they couldn’t get through.
The hack started at around 20:00 Bangladesh time on Thursday 4 February. But in New York it was Thursday morning, giving the Fed plenty of time to (unwittingly) carry out the hackers’ wishes while Bangladesh was asleep.
The next day, Friday, was the start of the Bangladeshi weekend, which runs from Friday to Saturday. So the bank’s HQ in Dhaka was beginning two days off. And when the Bangladeshis began to uncover the theft on Saturday, it was already the weekend in New York.
“So you see the elegance of the attack,” says US-based cyber-security expert Rakesh Asthana. “The date of Thursday night has a very defined purpose. On Friday New York is working, and Bangladesh Bank is off. By the time Bangladesh Bank comes back on line, the Federal Reserve Bank is off. So it delayed the whole discovery by almost three days.”
And the hackers had another trick up their sleeve to buy even more time. Once they had transferred the money out of the Fed, they needed to send it somewhere. So they wired it to accounts they’d set up in Manila, the capital of the Philippines. And in 2016, Monday 8 February was the first day of the Lunar New Year, a national holiday across Asia.
By exploiting time differences between Bangladesh, New York and the Philippines, the hackers had engineered a clear five-day run to get the money away.
They had had plenty of time to plan all of this, because it turns out the Lazarus Group had been lurking inside Bangladesh Bank’s computer systems for a year.
In January 2015, an innocuous-looking email had been sent to several Bangladesh Bank employees. It came from a job seeker calling himself Rasel Ahlam. His polite enquiry included an invitation to download his CV and cover letter from a website. In reality, Rasel did not exist – he was simply a cover name being used by the Lazarus Group, according to FBI investigators. At least one person inside the bank fell for the trick, downloaded the documents, and got infected with the viruses hidden inside.
Once inside the bank’s systems, Lazarus Group began stealthily hopping from computer to computer, working their way towards the digital vaults and the billions of dollars they contained.
And then they stopped.
Why did the hackers only steal the money a whole year after the initial phishing email arrived at the bank? Why risk being discovered while hiding inside the bank’s systems all that time? Because, it seems, they needed the time to line up their escape routes for the money.
Jupiter Street is a busy thoroughfare in Manila. Next to an eco-hotel and a dental surgery is a branch of RCBC, one of the country’s largest banks. In May 2015, a few months after the hackers accessed Bangladesh Bank’s systems, four accounts were set up here by the hackers’ accomplices. In hindsight, there were some suspicious signs: the driver’s licences used to set up the accounts were fakes, and the applicants all claimed to have exactly the same job title and salary, despite working at different companies. But no-one seemed to notice. For months the accounts sat dormant with their initial $500 deposit untouched while the hackers worked on other aspects of the plan.
By February 2016, having successfully hacked into Bangladesh Bank and created conduits for the money, the Lazarus Group was ready.
But they still had one final hurdle to clear – the printer on the 10th floor. Bangladesh Bank had created a paper back-up system to record all transfers made from its accounts. This record of transactions risked exposing the hackers’ work instantly. And so they hacked into the software controlling it and took it out of action.
With their tracks covered, at 20:36 on Thursday 4 February 2016, the hackers began making their transfers – 35 in all, totalling $951m, almost the entire contents of Bangladesh Bank’s New York Fed account. The thieves were on their way to a massive payday – but just as in a Hollywood heist movie, a single, tiny detail would catch them out.
As Bangladesh Bank discovered the missing money over the course of that weekend, they struggled to work out what had happened. The bank’s governor knew Rakesh Asthana and his company, World Informatix, and called him in for help. At this point, Asthana says, the governor still thought he could claw back the stolen money. As a result, he kept the hack secret – not just from the public, but even from his own government.
Meanwhile, Asthana was discovering just how deep the hack went. He found out the thieves had gained access to a key part of Bangladesh Bank’s systems, called Swift. It’s the system used by thousands of banks around the world to co-ordinate transfers of large sums between themselves. The hackers didn’t exploit a vulnerability in Swift – they didn’t need to – so as far as Swift’s software was concerned the hackers looked like genuine bank employees.
It soon became clear to Bangladesh Bank’s officials that the transactions couldn’t just be reversed. Some money had already arrived in the Philippines, where the authorities told them they would need a court order to start the process to reclaim it. Court orders are public documents, and so when Bangladesh Bank finally filed its case in late February, the story went public and exploded worldwide.
The consequences for the bank’s governor were almost instant. “He was asked to resign,” says Asthana. “I never saw him again.”
US Congresswoman Carolyn Maloney remembers clearly where she was when she first heard about the raid on Bangladesh Bank. “I was leaving Congress and going to the airport and reading about the heist, and it was fascinating, shocking – a terrifying incident, probably one of the most terrifying that I’ve ever seen for financial markets.”
As a member of the congressional Committee on Financial Services, Maloney saw the bigger picture: with Swift underpinning so many billions of dollars of global trade, a hack like this could fatally undermine confidence in the system.
She was particularly concerned by the involvement of the Federal Reserve Bank. “They were the New York Fed, which usually is so careful. How in the world did these transfers happen?”
Maloney contacted the Fed, and staff explained to her that most of the transfers had in fact been prevented – thanks to a tiny, coincidental detail.
The RCBC bank branch in Manila to which the hackers tried to transfer $951m was in Jupiter Street. There are hundreds of banks in Manila that the hackers could have used, but they chose this one – and the decision cost them hundreds of millions of dollars.
“The transactions… were held up at the Fed because the address used in one of the orders included the word ‘Jupiter’, which is also the name of a sanctioned Iranian shipping vessel,” says Carolyn Maloney.
Just the mention of the word “Jupiter” was enough to set alarm bells ringing in the Fed’s automated computer systems. The payments were reviewed, and most were stopped. But not all. Five transactions, worth $101m, crossed this hurdle.
Of that, $20m was transferred to a Sri Lankan charity called the Shalika Foundation, which had been lined up by the hackers’ accomplices as one conduit for the stolen money. (Its founder, Shalika Perera, says she believed the money was a legitimate donation.) But here again, a tiny detail derailed the hackers’ plans. The transfer was made to the “Shalika Fundation”. An eagle-eyed bank employee spotted the spelling mistake and the transaction was reversed.
And so $81m got through. Not what the hackers were aiming for, but the lost money was still a huge blow for Bangladesh, a country where one in five people lives below the poverty line.
By the time Bangladesh Bank began its efforts to claw the money back, the hackers had already taken steps to make sure it stayed beyond reach.
On Friday 5 February, the four accounts set up the previous year at the RCBC branch in Jupiter Street suddenly sprang to life.
The money was transferred between accounts, sent to a currency exchange firm, swapped into local currency and re-deposited at the bank. Some of it was withdrawn in cash. For experts in money laundering, this behaviour makes perfect sense.
“You have to make all of that criminally derived money look clean and look like it has been derived from legitimate sources in order to protect whatever you do with the money afterwards,” says Moyara Ruehsen, director of the Financial Crime Management Programme at the Middlebury Institute of International Studies in Monterey, California. “You want to make the money trail as muddy and obscure as possible.”
Even so, it was still possible for investigators to trace the path of the money. To make it completely untrackable it had to leave the banking system.
The Solaire sits on the waterfront in Manila, a gleaming white palace of hedonism, home to a hotel, a huge theatre, high-end shops and – its most famous attraction – a sprawling casino floor. Manila has become a big draw for gamblers from mainland China, where the pastime is illegal, and the Solaire is “one of the most elegant casino floors in Asia”, according to Mohammed Cohen, editor-at-large of Inside Asian Gaming Magazine. “It’s really beautifully designed, comparable to anything in south-east Asia. It has roughly 400 gaming tables and about 2,000 slot machines.”
It was here in Manila’s glitzy casino scene that the Bangladesh Bank thieves mounted the next stage of their money laundering operation. Of the $81m that washed through the RCBC bank, $50m was deposited in accounts at the Solaire and another casino, the Midas. (What happened to the other $31m? According to a Philippines Senate Committee set up to investigate, it was paid to a Chinese man called Xu Weikang, who’s believed to have left town on a private jet and never been heard of since.)
The idea of using casinos was to break the chain of traceability. Once the stolen money had been converted into casino chips, gambled over the tables, and changed back into cash, it would be almost impossible for investigators to trace it.
But what about the risks? Aren’t the thieves in danger of losing the loot across the casino tables? Not at all.
Firstly, instead of playing in the public parts of the casino, the thieves booked private rooms and filled them with accomplices who would play at the tables; this gave them control over how the money was gambled. Secondly, they used the stolen money to play Baccarat – a wildly popular game in Asia, but also a very simple one. There are only three outcomes on which to bet, and a relatively experienced player can recoup 90% or more of their stake (an excellent outcome for money launderers, who often get a far smaller return). The criminals could now launder the stolen funds and look forward to a healthy return – but to do so would take careful management of the players and their bets, and that took time. For weeks, the gamblers sat inside Manila’s casinos, washing the money.
Bangladesh Bank, meanwhile, was catching up. Its officials had visited Manila and identified the money trail. But when it came to the casinos, they hit a brick wall. At that time, the Philippines gambling houses were not covered by money laundering regulations. So far as the casinos were concerned, the cash had been deposited by legitimate gamblers, who had every right to fritter it away over the tables. (The Solaire casino says it had no idea it was dealing with stolen funds, and is co-operating with the authorities. The Midas did not respond to requests for comment.)
The bank’s officials managed to recover $16m of the stolen money from one of the men who organised the gambling jaunts at the Midas casino, called Kim Wong. He was charged, but the charges were later dropped. The rest of the money, however – $34m – was leaching away. Its next stop, according to investigators, would take it one step closer to North Korea.
Macau is an enclave of China, similar in constitution to Hong Kong. Like the Philippines, it’s a hotspot for gambling and home to some of the world’s most prestigious casinos. The country also has long-established links to North Korea. It was here that North Korean officials were in the early 2000s caught laundering counterfeit $100 notes of extremely high quality – so-called “Superdollars” – which US authorities claim were printed in North Korea. The local bank they laundered them through was eventually placed on a US sanctions list thanks to its connections with the Pyongyang regime.
It was also in Macau that a North Korean spy was trained before she bombed a Korean Air flight in 1987, killing 115 people. And it was in Macau that Kim Jong-un’s half brother, Kim Jong-nam, lived in exile before being fatally poisoned in Malaysia in an assassination many believe was authorised personally by the North Korean leader.
As the money stolen from Bangladesh Bank was laundered through the Philippines, numerous links to Macau started to emerge. Several of the men who organised the gambling jaunts in the Solaire were traced back to Macau. Two of the companies that had booked the private gambling rooms were also based in Macau. Investigators believe most of the stolen money ended up in this tiny Chinese territory, before being sent back to North Korea.
At night, North Korea famously appears to be a black hole in photos taken from outer space by Nasa, due to the lack of electricity in most parts of the country – in stark contrast to South Korea, which explodes with light at all hours of the day and night. North Korea ranks among the 12 poorest nations in the world, with an estimated GDP of just $1,700 per person – less than Sierra Leone and Afghanistan, according to the CIA.
And yet North Korea has produced some of the world’s most brazen and sophisticated hackers, it appears.
Understanding how, and why, North Korea has managed to cultivate elite cyber-warfare units requires looking at the family that has ruled North Korea since its inception as a modern nation in 1948: the Kims.
Founder Kim Il-sung built the nation officially known as the Democratic People’s Republic of Korea on a political system that is socialist but operates more like a monarchy.
His son, Kim Jong-il, relied on the military as his power base, provoking the US with tests of ballistic missile and nuclear devices. In order to fund the programme, the regime turned to illicit methods, according to US authorities – including the highly sophisticated counterfeit Superdollars.
Kim Jong-il also decided early on to incorporate cyber into the country’s strategy, establishing the Korea Computer Centre in 1990. It remains the heart of the country’s IT operations.
When, in 2010, Kim Jong-un – Kim Jong-il’s third son – was revealed as his heir apparent, the regime unfurled a campaign to portray the future leader, only in his mid-20s and unknown to his people, as a champion of science and technology. It was a campaign designed to secure his generation’s loyalty and to inspire them to become his warriors, using these new tools.
The young Kim, who took power in late 2011 upon his father’s death, called nuclear weapons a “treasured sword”, but he too needed a way to fund them – a task complicated by the ever tighter sanctions imposed by the UN Security Council after the country’s first tests of a nuclear device and a long-range ballistic missile in 2006. Hacking was one solution, US authorities say.
The embrace of science and technology did not extend to allowing North Koreans to freely connect to the global internet, though – that would enable too many to see what the world looks like outside their borders, and to read accounts that contradict the official mythology.
So in order to train its cyber-warriors, the regime sends the most talented computer programmers abroad, mostly to China.
There they learn how the rest of the world uses computers and the internet: to shop, to gamble, to network and to be entertained. It’s there, experts say, that they are transformed from mathematical geniuses into hackers.
Scores of these young men are believed to live and work in North Korean-run outposts in China.
“They are very good at masking their tracks but sometimes, just like any other criminal, they leave crumbs, evidence behind,” says Kyung-jin Kim, a former FBI Korea chief who now works as a private sector investigator in Seoul. “And we’re able to identify their IP addresses back to their location.”
Those crumbs led investigators to an unassuming hotel in Shenyang, in China’s north-east, guarded by a pair of stone tigers, a traditional Korean motif. The hotel was called the Chilbosan, after a famous mountain range in North Korea.
Photos posted to hotel review sites such as Agoda reveal charming Korean touches: colourful bedspreads, North Korean cuisine and waitresses who sing and dance for their customers.
It was “well-known in the intel community”, says Kyung-jin Kim, that suspected North Korean hackers were operating from the Chilbosan when they first broke on to the world stage in 2014.
Meanwhile, in the Chinese city of Dalian, where Park Jin-hyok is believed to have lived for a decade, a community of computer programmers was living and working in a similar North-Korea-run operation, says defector Hyun-seung Lee.
Lee was born and raised in Pyongyang but lived for years in Dalian, where his father was a well-connected businessman working for the North Korean government – until the family defected in 2014. The bustling port city across the Yellow Sea from North Korea was home to about 500 North Koreans when he was living there, Lee says.
Among them, more than 60 were programmers – young men he got to know, he says, when North Koreans gathered for national holidays, such as Kim Il-sung’s birthday.
One of them invited him over to their living quarters. There, Lee saw “about 20 people living together and in one space. So, four-to-six people living in one room, and then the living room they made it like an office – all the computers, all in the living room.”
They showed him what they were producing: mobile phone games that they were selling to South Korea and Japan through brokers, making $1m per year.
Although North Korean security officials kept a close eye on them, life for these young men was still relatively free.
“It’s still restricted, but compared to North Korea, they have much freedom so that they can access the internet and then they can watch some movies,” Lee says.
After about eight years in Dalian, Park Jin-hyok appears to have been anxious to return to Pyongyang. In a 2011 email intercepted by the FBI, he mentions wanting to marry his fiancee. But it would be a few more years before he was allowed to do this.
The FBI says his superiors had another mission for him: a cyber-attack on one of the world’s largest entertainment companies – Sony Pictures Entertainment in Los Angeles, California. Hollywood.
In 2013, Sony Pictures announced the making of a new movie starring Seth Rogen and James Franco that would be set in North Korea.
It’s about a talk show host, played by Franco, and his producer, played by Rogen. They go to North Korea to interview Kim Jong-un, and are persuaded by the CIA to assassinate him.
North Korea threatened retaliatory action against the US if Sony Pictures Entertainment released the film, and in November 2014 an email was sent to company bosses from hackers calling themselves the Guardians of Peace, threatening to do “great damage”.
Three days later a horror-film image of a blood-red skeleton with fangs and glaring eyes appeared on employees’ computer screens. The hackers had made good on their threats. Executives’ salaries, confidential internal emails, and details of as-yet unreleased films were leaked online – and the company’s activities ground to a halt as its computers were disabled by the hackers’ viruses. Staff couldn’t swipe passes to enter their offices or use printers. For a full six weeks a coffee shop on the MGM lot, the HQ of Sony Pictures Entertainment, was unable to take credit cards.
Sony had initially pressed ahead with plans to release The Interview in the usual way, but these were hastily cancelled when the hackers threatened physical violence. Mainstream cinema chains said they wouldn’t show the film, so it was released only digitally and in some independent cinemas.
But the Sony attack, it turns out, may have been a dry run for an even more ambitious hack – the 2016 bank heist in Bangladesh.
Bangladesh is still trying to recover the rest of its stolen money – around $65m. Its national bank is taking legal action against dozens of people and institutions, including RCBC bank, which denies breaching any rules.
As skilful as the hacking of Bangladesh Bank was, just how pleased would the Pyongyang regime have been with the end result? After all, the plot started out as a billion-dollar heist, and the eventual haul would have been only in the tens of millions. Hundreds of millions of dollars had been lost as the thieves had navigated the global banking system, and tens of millions more as they paid off middlemen. In future, according to US authorities, North Korea would find a way to avoid this attrition.
In May 2017, the WannaCry ransomware outbreak spread like wildfire, scrambling victims’ files and charging them a ransom of several hundred dollars to retrieve their data, paid using the virtual currency Bitcoin. In the UK, the National Health Service was particularly badly hit; accident and emergency departments were affected, and urgent cancer appointments had to be rescheduled.
As investigators from the UK’s National Crime Agency delved into the code, working with the FBI, they found striking similarities with the viruses used to hack into Bangladesh Bank and Sony Pictures Entertainment, and the FBI eventually added this attack to the charges against Park Jin-hyok. If the FBI’s allegations are correct, it shows North Korea’s cyber army had now embraced cryptocurrency – a vital leap forward because this high-tech new form of money largely bypasses the traditional banking system – and could therefore avoid costly overheads, such as pay-offs to middlemen.
WannaCry was just the start. In the ensuing years, tech security firms have attributed many more cryptocurrency attacks to North Korea. They claim the country’s hackers have targeted exchanges where cryptocurrencies like Bitcoin are swapped for traditional currencies. Added together, some estimates put the thefts from these exchanges at more than $2bn.
And the allegations keep coming. In February the US Department of Justice charged two other North Koreans, whom they claim are also members of the Lazarus Group and are linked to a money-laundering network stretching from Canada to Nigeria.
Computer hacking, global money laundering, cutting edge cryptocurrency thefts… If the allegations against North Korea are true, then it appears many people have underestimated the country’s technical skill and the danger it presents.
But this also paints a disturbing picture of the dynamics of power in our increasingly connected world, and our vulnerability to what security experts call “asymmetric threat” – the ability of a smaller adversary to exercise power in novel ways that make it a far bigger threat than its size would indicate.
Investigators have uncovered how a tiny, desperately poor nation can silently reach into the email inboxes and bank accounts of the rich and powerful thousands of miles away. They can exploit that access to wreak havoc on their victims’ economic and professional lives, and drag their reputations through the mud. This is the new front line in a global battleground: a murky nexus of crime, espionage and nation-state power-mongering. And it’s growing fast.
Geoff White is the author of Crime Dot Com: From Viruses to Vote Rigging, How Hacking Went Global. Jean H Lee opened Associated Press’s Pyongyang bureau in 2012; she is now a senior fellow at the Wilson Center in Washington DC.
– BBC News
Features
Driving high-tech exports: The pivotal role of R&D

 High-tech exports serve as a critical driver of economic growth and global competitiveness for nations. In an era marked by rapid technological advancements and globalization, the ability of a country to expand its high-tech exports hinges significantly on its investment in research and development (R&D). By fostering innovation, enhancing product quality, and improving production efficiency, R&D plays a pivotal role in determining a country’s success in the high-tech export sector. This essay explores the significance of R&D in driving high-tech exports, highlighting its impact on product innovation, international competitiveness, and economic sustainability. Figure 1 compares High-Tech Exports among India, Malaysia and Sri Lanka. (See Graph 01)
High-tech exports serve as a critical driver of economic growth and global competitiveness for nations. In an era marked by rapid technological advancements and globalization, the ability of a country to expand its high-tech exports hinges significantly on its investment in research and development (R&D). By fostering innovation, enhancing product quality, and improving production efficiency, R&D plays a pivotal role in determining a country’s success in the high-tech export sector. This essay explores the significance of R&D in driving high-tech exports, highlighting its impact on product innovation, international competitiveness, and economic sustainability. Figure 1 compares High-Tech Exports among India, Malaysia and Sri Lanka. (See Graph 01)
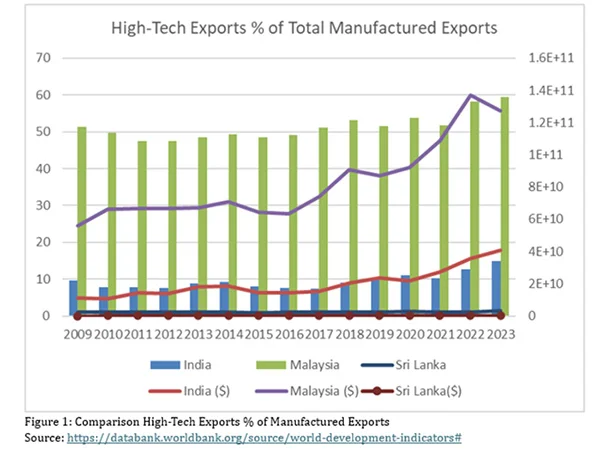
The Link Between R&D and High-Tech Exports
R&D is the backbone of high-tech industries, enabling firms to develop cutting-edge products and services that cater to evolving global market demands. Technological innovations, resulting from R&D investments, enhance the quality, efficiency, and uniqueness of products, making them more attractive to international buyers. Countries with robust R&D ecosystems, such as the United States, Germany, and South Korea, have consistently led the world in high-tech exports. Their ability to create and commercialize innovative technologies underscores the direct correlation between R&D spending and export growth in the high-tech sector. Figure 2 compares High-Tech Exports and Research and Development expenses among India, Malaysia and Sri Lanka. (See Graph 2)
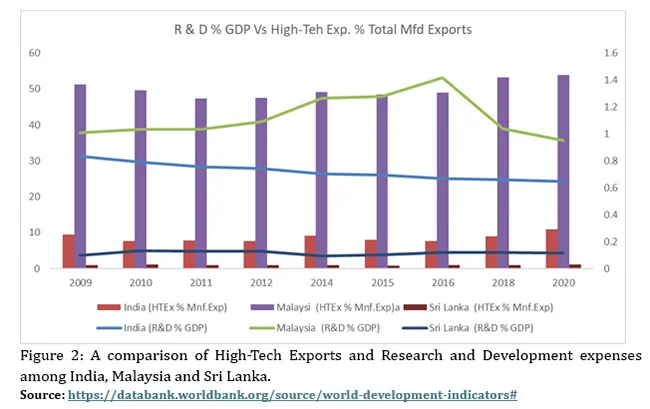
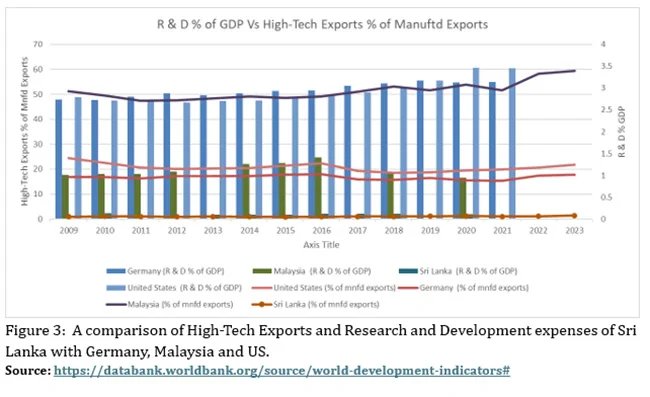
Figure 3 shows a comparison of High-Tech Exports and Research and Development expenses of Sri Lanka with Germany, Malaysia and the US. (See Graph 03)
Other Factors Influencing High-Tech Exports
While R&D is the primary driver of high-tech exports, several other factors also influence a country’s ability to compete in global technology markets. These include:
* Infrastructure and Logistics:
Efficient infrastructure, including transportation networks, digital connectivity, and advanced manufacturing facilities, is crucial for exporting high-tech products. However, without strong R&D, infrastructure alone cannot drive technological advancements.
* Trade Policies and Regulations:
Favourable trade policies, such as low tariffs, export incentives, and intellectual property protections, facilitate high-tech exports. Yet, without continuous innovation from R&D, trade policies alone cannot sustain competitiveness.
* Human Capital and Skilled Workforce:
A highly educated and technically skilled workforce is essential for high-tech industries. While talent is important, it must be complemented by R&D investments to create and commercialize innovations.
* Foreign Direct Investment (FDI):
FDI brings capital, expertise, and market access, enhancing a country’s ability to export high-tech products. However, nations that do not invest in R&D risk becoming mere assembly hubs rather than innovation leaders.
* Access to Capital and Financial Support:
Access to venture capital, government funding, and financial incentives supports high-tech industries. Yet, financial resources alone do not guarantee technological progress without active R&D efforts.
Why R&D is the Most Powerful Factor
Despite the influence of these factors, R&D remains the most powerful driver of high-tech exports because it is the source of continuous innovation and competitive advantage. Infrastructure, policies, human capital, and financial support can facilitate high-tech exports, but without groundbreaking research and new technological developments, a country risks stagnation in global markets. Nations that lead in high-tech exports—such as the US, Japan, and China—have consistently prioritized R&D, enabling them to pioneer new technologies and set industry standards.
Enhancing International Competitiveness
A strong R&D culture equips businesses with the ability to maintain a competitive edge in global markets. By developing proprietary technologies and advanced manufacturing processes, firms can reduce production costs, improve product functionality, and increase overall efficiency. This, in turn, enhances their competitive standing in international markets, allowing them to secure long-term trade relationships. Additionally, R&D-driven innovation fosters brand reputation and consumer trust, leading to increased demand for high-tech exports.
Economic Sustainability and Knowledge-Based Growth
Investing in R&D facilitates long-term economic sustainability by transitioning economies from resource-based models to knowledge-driven ones. High-tech exports contribute significantly to GDP growth, employment generation, and foreign exchange earnings. Countries that prioritize R&D in their high-tech sectors experience increased productivity, reduced dependency on traditional industries, and higher value-added output. Moreover, R&D fosters entrepreneurship and the development of start-ups, further strengthening the high-tech export ecosystem.
The Role of Government Policies and Industry Collaboration
Governments play a crucial role in fostering R&D through policy frameworks, financial incentives, and strategic collaborations. Public-private partnerships, tax incentives, and funding for research institutions are essential mechanisms that stimulate innovation. Additionally, collaboration between universities and industries facilitates technology transfer and the commercialization of research outcomes, leading to the development of exportable high-tech products.
The most appropriate and suitable types of R&D for driving high-tech exports include:
1. Applied Research
Applied research is crucial for fostering high-tech exports as it focuses on developing new technologies with immediate commercial applications. Unlike basic research, which is theoretical in nature, applied research is directed toward practical outcomes that enhance global competitiveness. For example, advancements in nanotechnology and artificial intelligence (AI) have significantly contributed to the global expansion of semiconductor and automation industries. Furthermore, applied research helps in bridging the gap between scientific discovery and market implementation, ensuring that new technologies can be effectively utilized in high-tech exports.
2. Product Development R&D
Product development R&D plays a key role in creating innovative products with unique features, enabling firms to differentiate themselves in international markets. It involves activities, such as prototype testing, performance enhancement, and feature innovation, which contribute to the competitive advantage of high-tech firms. For instance, the global smartphone industry continuously invests in R&D to develop new functionalities, improve user experience, and introduce cutting-edge designs, thereby sustaining consumer demand in highly competitive markets. The strategic focus on product innovation allows firms to maintain premium pricing and brand loyalty in high-tech sectors.
3. Process Innovation R&D
Process innovation R&D enhances production efficiency and cost-effectiveness, making high-tech exports more competitive in price-sensitive markets. This type of R&D focuses on improving manufacturing techniques, reducing waste, and integrating automation to optimize resource utilization. For example, the use of additive manufacturing (3D printing) in aerospace and biomedical industries has resulted in cost reductions and faster production cycles, leading to improved market penetration of high-tech exports. Companies that invest in process innovation are able to achieve economies of scale and maintain long-term cost advantages in global markets.
4. Collaborative R&D
Collaborative R&D, involving partnerships between academia, industry, and government, accelerates the commercialization of new technologies. Public-private partnerships (PPPs) facilitate knowledge exchange, reduce R&D costs, and increase the likelihood of successful innovation. A notable example is the European Union’s Horizon 2020 programme, which funds cross-border collaborative research to enhance industrial competitiveness and technological leadership. Additionally, collaboration between multinational corporations and research institutions has led to breakthrough innovations in biotechnology, renewable energy, and telecommunications. By leveraging diverse expertise and shared resources, collaborative R&D enhances the scalability and global reach of high-tech exports.
5. Market-Driven R&D
Market-driven R&D aligns research efforts with global consumer trends and regulatory requirements to maximize export potential. Unlike traditional R&D approaches that focus solely on technological advancements, market-driven R&D emphasizes consumer needs, sustainability, and compliance with international standards. For example, the increasing demand for environmentally friendly products has prompted R&D investments in electric vehicles (EVs) and sustainable packaging solutions, ensuring market acceptance and regulatory approval in various regions. Companies that integrate market intelligence into their R&D strategies are better positioned to develop products that meet international demand, enhance brand reputation, and drive high-tech export growth.
Conclusion
R&D stands as a cornerstone in driving high-tech exports, shaping a nation’s ability to compete in the global economy. While factors such as infrastructure, trade policies, human capital, FDI, and financial support play a role in high-tech exports, they are secondary to the fundamental necessity of continuous innovation. By fostering technological advancements, enhancing competitiveness, and promoting economic sustainability, R&D investments serve as the ultimate catalyst for high-tech export growth. Countries aiming to strengthen their high-tech export sectors must prioritize R&D policies and create an ecosystem that supports innovation, ensuring long-term prosperity in an increasingly technology-driven world.
Investing in different types of R&D is essential for fostering high-tech exports. Applied research drives technological advancements, product development R&D ensures market differentiation, and process innovation R&D enhances cost efficiency. Additionally, collaborative R&D accelerates innovation through strategic partnerships, while market-driven R&D ensures alignment with global consumer trends and regulatory standards. A comprehensive approach that incorporates all these R&D types will enable firms to sustain their competitive advantage and expand their presence in the global high-tech market.
(The writer, a senior Chartered Accountant and professional banker, is Professor at SLIIT University, Malabe. He is also the author of the “Doing Social Research and Publishing Results”, a Springer publication (Singapore), and “Samaja Gaveshakaya (in Sinhala). The views and opinions expressed in this article are solely those of the author and do not necessarily reflect the official policy or position of the institution he works for. He can be contacted at saliya.a@slit.lk and www.researcher.com)
Features
Will NPP continue Sri Lanka’s path of Economic Suicide?

By Sunil Abhayawardhana
Though Sri Lanka has a new government, its first budget for 2025 remains within the conditions and targets of the ongoing IMF programme (which will continue until the end of 2027).
A major shortfall in the budget is the lack of a ‘developmental thrust,’ which is essential for the country to grow out of the current crisis. Rather than discussing the minutiae of the budget, it is worth looking at how Sri Lanka got into this situation by making the same mistakes over and over again.
Though these mistakes can be pointed out, mainstream economists prefer to stick to the outdated textbook economics taught at university even when proven wrong. Therefore, the best way to bring up Sri Lanka’s mistakes is through a comparative approach with the High Performing Asian Economies (HPAEs).
Missed Opportunities
At independence in 1948, Sri Lanka (then Ceylon) was expected to develop rapidly due to advantages such as its strategic location, which was expected to be a multiplier by itself. This ‘strategic location’ has not fully been made use of to this day.
The oil tank farm in Trincomalee was a big storage facility in 1948. If the government had negotiated to buy the facility from the British (which was finally done in 1965 for 250,000 sterling pounds) and set up a refinery, Trincomalee could have become the oil hub of Asia, long before Singapore. This could have saved the country from the perennial forex crisis that it had to deal with due to the diminishing returns from the plantation economy.
The plantation economy had reached its peak over two decades before Independence and was not able to sustain a growing population. Yet, the immediate post-Independence governments did nothing about this. Though funds were available, there was a deficit in the thinking and a lack of vision for the future. The lack of immediate effort to diversify and industrialise the economy was the first act of economic suicide.
At around the same time, HPAEs such as Japan, South Korea, and Taiwan (China) embarked on their development programmes, which have brought results far exceeding their own expectations. What was it that the HPAEs got so right, and what did Sri Lanka get so wrong?
A comparison between Sri Lanka and the HPAEs brings up many differences. The four major points of interest that stand out were as follows:
1) No plan
2) Bad theory
3) Bad advice
4) Not understanding development
No Plan
A sovereign country should know where it wants to go and how it hopes to reach its objectives. This is normally expressed in a development plan that provides the public with a clear roadmap. A plan becomes more necessary when countries start out from a very low level of development. An initial burst of energy is required before markets can take over.
A fair amount of strategic thinking goes into the formulation of such a plan. It should take into account the natural and human resources available and the strategic sectors that need development. The plan should aim to keep the cost of development as low as possible.
In a country with different communities, the plan should also unite people to work towards a common objective. A development plan looks not only at growth but also at the pattern of growth. When growth becomes more widespread, it opens up more opportunities for the public.
All HPAEs began their journeys with development plans covering many decades. Some countries, like China and Vietnam, still adhere to five-year plans. Sri Lanka is the one country that tried to develop without a plan. The World Bank mission of 1952 recommended a planning process for Sri Lanka, though it was hardly implemented. The first Ten-Year Plan of 1959 (which took three years to formulate) was never implemented. The Five-Year Plan of 1972 was derailed by the 1973 oil shock.
While Sri Lanka struggled to plan, the HPAEs were already implementing their plans and seeing results. Sri Lanka drifted to depending on ad-hoc methods without long-term objectives. Even after 77 years of Independence, the country is still unable to identify the sectors for industrial development.
Bad Theory
At independence, the country did not have much know-how in economics. The few who had been educated in economics at the UK universities were taught neoclassical economics with a Keynesian tinge. The Quantity Theory of Money (QTM) was the guiding orthodoxy of the time. What the QTM says is that if the quantity of money is increased, there would be a corresponding increase in prices and therefore inflation.
However, the HPAEs realised that if new money was directed towards investment in productive industry, the result would be an expansion of the economy rather than inflation. The bulk of their funds for development came from monetary financing from the Central Bank. They would have taken inspiration from examples such as Canada in the 1940s and Japan in the 1930s, both of which used monetary financing for specific purposes.
Another point to note is the fact that all the HPAEs had multiple development banks, which helped in the development drive. In contrast, Sri Lanka got rid of its two development banks on advice from the West, thereby reducing the availability of long-term credit for the development process.
Due to Sri Lanka’s adherence to the QTM, we have had to rely on other methods of finance, which has created a dependency on foreign aid and a huge foreign currency debt. Though there is so much evidence that monetary financing used wisely can bring great results, many in Sri Lanka still adhere to the QTM. While most universities still teach the old concepts, it is sad that students at the master’s level and beyond do not think for themselves.
Bad Advice
When a country lacks knowledge and experience, it becomes necessary to seek advice from others. The World Bank and the IMF did perform this function in the early days. However, since the neoliberal onslaught, the purpose of these institutions has taken a more politicised turn.
The advice given by the IMF and other international advice has to be analysed, as it often turns out to be more damaging. For example, austerity has been proven to be counterproductive and causes more damage to the economy and social life. The present advice the government is receiving from the IMF, the CBSL, and the Ministry of Finance is no different.
When South Korean President Park Chung-Hee was offered Western economic advisors, he knew exactly what their advice would be. So, he declined the offer and obtained economic advisors from Japan instead.
Sri Lanka, on the other hand, accepted whatever came from the West. Our leaders accepted the ‘Washington Consensus,’ which we follow to this day, even though the author of the document, John Williamson, has himself declared it a dead document.
Economists advise governments towards suicidal actions without observing what has been done around the world before. There are political aspects to this bad advice. As there is an overproduction of global money, such bad advice is actually beneficial to the Western financial sector and its political interests.
Not Understanding Development
Sri Lanka has still not understood what development means. This can be seen from the fact that despite having a potential 30,000 MW of wind power generation, the government wants to give this opportunity to foreign companies and buy back the power with foreign exchange. Even the export potential is given to foreign companies, while local companies lose that opportunity.
If such a situation had been in any of the HPAEs, they would have first developed a local windmill manufacturing industry to meet their needs. That is what development is – developing productive capabilities and creating a productive ecosystem. There are many opportunities that Sri Lanka has missed because the concept of development has not been understood.
Had local inventors been encouraged and supported, a true industrial base would have been flourishing today. One example is Ray Wijewardene’s hand tractor, to which one Sri Lankan asked, “Why do we need hand tractors when there are so many buffaloes around?”. Imagine what the HPAEs would have done with a brilliant, innovative mind like Ray Wijewardene’s.
Even the few sectors of industry built up to world-class levels have been destroyed by bad government policy. One such industry was the heavy construction industry, which is vital for infrastructure development. A local company had built up its capacity to do international projects funded by the World Bank and had performed many projects in the country, but the change of policy after 1977 destroyed the company and opened the doors to foreign companies at inflated prices, for which the country struggles to pay off its loans.
The local highway construction projects are an example, where Sri Lanka’s highways are considered the most expensive in the world, which opened opportunities for corruption. The very first industry developed in the HPAEs was the heavy construction industry in order to keep the cost of development low. Sri Lanka did the opposite.
Conclusion
It is quite clear that Sri Lanka’s present position is of its own making, following quite the opposite of what the HPAEs did. However, though many learn from mistakes, Sri Lanka does not seem to have learnt any lessons. Our advisors keep telling us to repeat our mistakes, and we keep listening to them.
It was expected that the NPP government would make a radical change in thinking, but it has not expressed any meaningful change of thinking with regard to major issues. Without such a change, Sri Lanka will continue on its suicidal path.
(Sunil Abhayawardhana was CEO of Sri Lanka’s largest heavy construction company. He has a master’s degree from the University of Wales and is working on a PhD in economics. He is a member of the Asia Progress Forum, which is a collective of like-minded intellectuals, professionals, and activists dedicated to building dialogue that promotes Sri Lanka’s sovereignty, development, and leadership in the Global South. APF can be contacted at asiaprogressforum@gmail.com).
Features
Coping with Batalanda’s emergence to centre stage

by Jehan Perera
The Batalanda Commission report which goes into details of what happened during the JVP insurrection of 1987-89 has become the centre of public attention. The controversy has long been a point of contention and a reminder of the country’s troubled past and entrenched divisions that still exist. The events that occurred at Batalanda during the violent suppression of the JVP-led insurgency, remain a raw wound, as seen in the sudden resurfacing of the issue. The scars of violence and war still run deep. At a time when the country is grappling with pressing challenges ranging from economic recovery to social stability, there is a need to keep in focus the broader goal of unity for long-term peace and prosperity. But the ghosts of the past need also to be put to rest without continuing to haunt the present and future.
Grisly accounts of what transpired at Batalanda now fill the social media even in the Tamil media, though Tamils were not specifically targeted at that time. There was then a ceasefire between the government and LTTE. The Indo-Lanka Accord had just been signed and the LTTE were fighting the Indian peacekeeping army. The videos that are now circulating on social media would show the Tamil people that they were not the only ones at the receiving end of counter-terrorist measures. The Sinhalese were in danger then, as it was a rebellion of Sinhalese against the state. Sinhalese youth had to be especially careful.
It appears that former president Ranil Wickremesinghe was caught unprepared by the questions from a team from Al Jazeera television. The answers he gave, in which he downplayed the significance of the Batalanda Commission report have been viewed differently, depending on the perspective of the observer. He has also made a statement in which he has rejected the report. The report, which demands introspection, referred to events that had taken place 37 years earlier. But the ghosts of the past have returned. After the issue has come to the fore, there are many relatives and acquaintances of the victims from different backgrounds who are demanding justice and offering to come forward to give evidence of what they had witnessed. They need closure after so many years.
MORE POLARISATION
The public reaction to the airing of the Al Jazeera television programme is a reminder that atrocities that have taken place cannot be easily buried. The government has tabled the Batalanda Commission report in parliament and hold a two-day debate on it. The two days were to be consecutive but now the government has decided to space them out over two months. There is reason to be concerned about what transpires in the debate. The atrocities that took place during the JVP insurrection involved multiple parties. Batalanda was not the only interrogation site or the only torture chamber. There were many others. Former president Ranil Wickremesinghe was not the only prominent protagonist in the events that transpired at that time.
The atrocities of the late 1980s were not confined to one location, nor were they the responsibility of a single individual or group. The JVP engaged in many atrocities and human rights violations. In addition to members of the former government and military who engaged in counter-terrorism operations there were also other groups that engaged both in self-defence and mayhem. These included members of left political parties who were targeted by the JVP and who formed their own para-military groups. Some of the leaders went on to become ministers in succeeding governments and even represented Sri Lanka at international human rights forums. Even members of the present government will not be able to escape the fallout of the debate over the Batalanda Commission report.
If the debate becomes a battleground for assigning blame rather than seeking solutions, it could have far-reaching consequences for Sri Lanka’s social and political stability. Economic recovery, governance reform, and development require stability and cooperation. The present storm caused by the Batalanda Commission report, and the prospects for increased polarisation and hatred do not bode well for the country. Rather than engaging in potentially divisive debates that could lead to further entrenchment of opposing narratives, Sri Lanka would be better served by a structured and impartial approach to truth-seeking and reconciliation.
NATIONAL HEALING
Earlier this month at the UN Human Rights Council in Geneva, the government rejected the UN High Commissioner for Human Rights assertion that the external evidence gathering unit would continue to collect evidence on human rights violations in Sri Lanka. This evidence gathering unit has a mandate to collect information on a wide range of human rights violations including intimidation and killings of journalists but with a focus on the human rights violations and war crimes during the course of the LTTE war and especially at its end. The government’s position has been that it is determined to deal with human rights challenges including reconciliation through domestic processes.
Addressing the High-Level Segment of the 58th Regular Session of the United Nations Human Rights Council (UNHRC) in Geneva in February this year, Foreign Minister Vijitha Herath said: “The contours of a truth and reconciliation framework, will be further discussed with the broadest possible cross section of stakeholders, before operationalisation to ensure a process that has the trust of all Sri Lankans. Our aim is to make the domestic mechanisms credible and sound within the constitutional framework. This will include strengthening the work towards a truth and reconciliation commission empowered to investigate acts of violence caused by racism and religious extremism that give rise to tensions within Sri Lankan society.”
The concept of a truth and reconciliation commission was first broached in 2015 by then prime minister Ranil Wickremesinghe’s government. In 2019 after winning the presidential elections, former president Gotabaya Rajapaksa too saw merit in the idea, but neither of these two leaders had the commitment to ensure that the process was completed. Promoting reconciliation in Sri Lanka among divergent political actors with violent political pasts requires a multi-faceted approach that blends political, social, and psychological strategies.
Given the country’s complex history of armed conflict, ethnic tensions, and political polarisation, the process must be carefully designed to build trust, address grievances, and create a shared vision for the future. A truth and reconciliation process as outlined in Geneva by the government, which has teeth in it for both punishment and amnesty, can give the country the time and space in which to uncover the painful truths and the path to national healing.
-

 Foreign News4 days ago
Foreign News4 days agoSearch continues in Dominican Republic for missing student Sudiksha Konanki
-

 Features6 days ago
Features6 days agoRichard de Zoysa at 67
-

 Features3 days ago
Features3 days agoThe Royal-Thomian and its Timeless Charm
-

 News4 days ago
News4 days agoDPMC unveils brand-new Bajaj three-wheeler
-

 Features6 days ago
Features6 days agoSL Navy helping save kidneys
-

 Features3 days ago
Features3 days ago‘Thomia’: Richard Simon’s Masterpiece
-

 Latest News5 days ago
Latest News5 days agoDebutant Madara, Athapaththu fashion Sri Lanka women’s first T20I win in New Zealand
-

 Features5 days ago
Features5 days agoWomen’s struggles and men’s unions











